Get the Latest HR Insights & Analysis
Get the latest insights and analysis from AIHR’s Chief HR Scientist, Dr. Dieter Veldsman, delivered to your inbox every first Thursday of the month.
Featured Insights
HR Trends 2025 Report
In the world of work, change is desperately needed. In this report, Founder of AIHR Erik van Vulpen and AIHR’s Chief HR Scientist Dieter Veldsman outline how HR can take action to elevate work embrace disruption in the world of work in 2025.
Get the essential information about the 11 trends shaping HR right now.

Deep Dive with our HR Dialogues
Listen to the HR Dialogues Podcast
 The Evolving CHRO Role: Skills, Impact & ClichésDecember 15, 2022
The Evolving CHRO Role: Skills, Impact & ClichésDecember 15, 2022 Total Well-Being and Rewards: How Microsoft Does ItDecember 1, 2022
Total Well-Being and Rewards: How Microsoft Does ItDecember 1, 2022 Purpose at Work: What Does the Future Hold?November 10, 2022
Purpose at Work: What Does the Future Hold?November 10, 2022 Unretirement: It’s Time to Rethink Age in the WorkplaceOctober 27, 2022
Unretirement: It’s Time to Rethink Age in the WorkplaceOctober 27, 2022 How HR is Managing Rising Inflation in Startups & ScaleupsOctober 13, 2022
How HR is Managing Rising Inflation in Startups & ScaleupsOctober 13, 2022
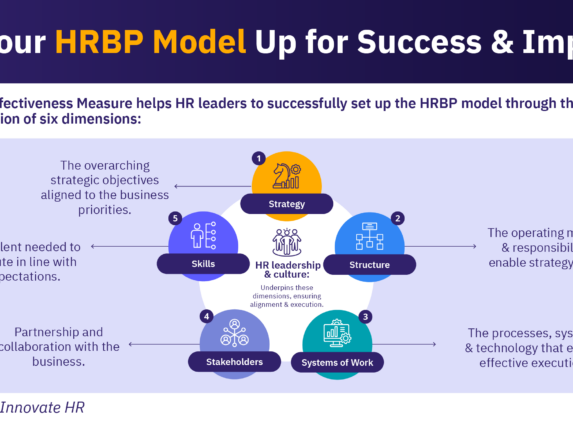
HRBP Impact Assessment
Is your HRBP model achieving maximum impact? Take the HRBP Impact Assessment and instantly get a detailed report with actionable recommendations to help drive better business results.
LEARN MORE
Upcoming Events
Featured External Contributions
Build better HR teams, faster
Set your HR team up for success. Whether you're a team of 10 to 1,000, AIHR is the only HR learning platform you will ever need to upskill at scale.1
Personalized Upskilling
Design a learning journey that is tailored to the specific learning needs of your HR organization.
HR Resource Library
Never start from scratch by downloading off-the-shelf templates and guides.
Live Events & Webinars
Stay up-to-date with the latest HR Practices by joining weekly live events (or watching the replay).
AIHR Copilot
Never get stuck again with trustworthy, expert-level, answers to your questions.
Learning Consulting
Day-to-day support for learners to ensure they get their questions answered and reach their goals.
Global HR Community
Join discussions and learn from thousands of talented peers and HR Subject Matter Experts.