Verbal Reprimand
What is a verbal reprimand?
A verbal reprimand is a disciplinary measure employers utilize to address employee behavior or performance concerns through oral communication. This approach entails engaging the employee in a private conversation to express concerns, clarify expectations, and outline potential consequences.
Verbal reprimands are frequently employed as an initial step in addressing behavioral or performance issues. They allow employees to rectify their actions before more serious disciplinary measures are implemented.
Verbal reprimand vs. written reprimand
The table below demonstrates the key differences between the two terms:
Form of communication
Oral communication
Written communication
Formality level
Less formal
More formal
Purpose
Address minor issues early on and provide immediate feedback
Address more serious or recurring issues with formal documentation
Record keeping
Only noted by the manager or HR, not as part of the employee’s official record
Becomes part of the employee’s permanent record
Impact on employment
Generally seen as a corrective measure
Can have stronger implications for future employment actions, such as promotions or a termination
Examples
• Minor policy violations
• Tardiness
• Initial instances of performance issues
• Major policy violations
• Continued tardiness despite verbal warnings
• Severe performance issues
Follow-up
Often includes an informal follow-up discussion
Often includes formal follow-up meetings and reviews
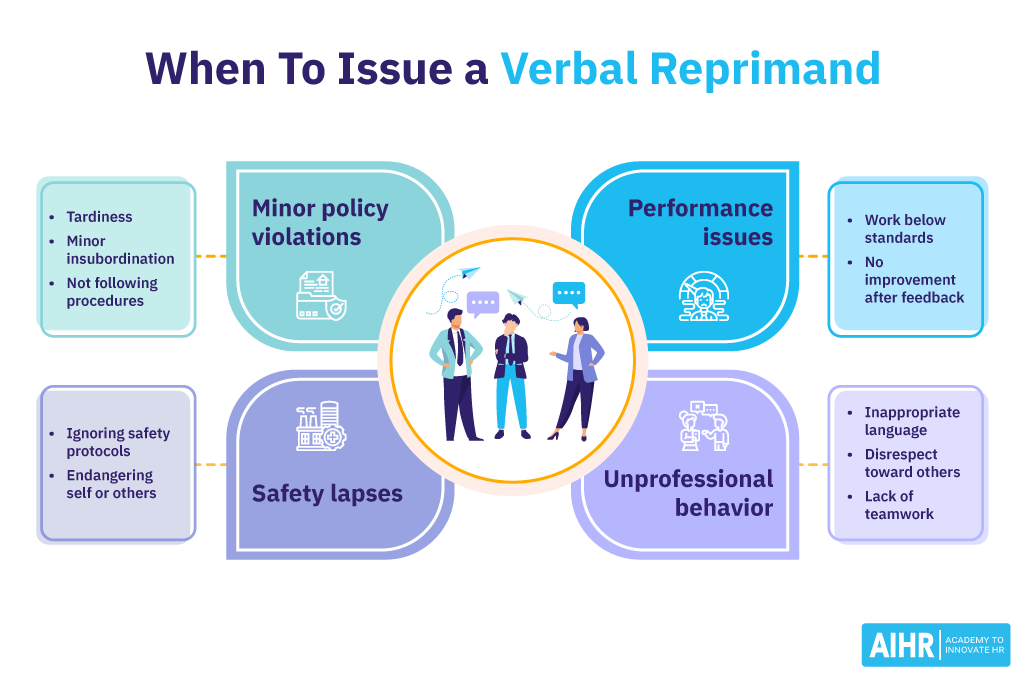
When to issue a verbal reprimand
A verbal reprimand is an effective tool for addressing minor infractions, performance issues, or behavioral concerns in a professional and constructive manner. It serves as an early intervention to correct issues before they escalate. Here are common situations where issuing a verbal reprimand is appropriate:
- Minor policy violations: This includes minor violations of workplace rules or policies, such as tardiness, minor insubordination, or failure to follow specific procedures.
- Performance issues: When an employee’s work performance falls below established standards, and initial feedback or coaching has not resulted in improvement.
- Unprofessional behavior: If an employee demonstrates unprofessional behavior, such as inappropriate language, disrespect towards colleagues or clients, or failure to cooperate with their team.
- Safety lapses: If an employee neglects safety protocols and endangers themselves or others, immediate verbal correction is crucial even if no harm has occurred.
Verbal reprimand example
When delivering a verbal reprimand, it’s crucial to be clear, concise, and constructive. The goal is to address the issue, explain its impact, and provide guidance for improvement while maintaining a professional and supportive tone.
Suppose an employee named Alex has consistently been late to work over the past few weeks. Here is an example of a verbal reprimand script:
Manager: “Thank you for taking the time to speak with me. I want to discuss a concern regarding your punctuality. Over the past few weeks, I’ve noticed you’ve been arriving late to work frequently. Specifically, you’ve been late on several occasions, which has started to affect team operations.”
Alex: “I’m sorry about that. I’ve been having some trouble with my morning commute — there have been a lot of delays.”
Manager: “I understand that sometimes unforeseen circumstances can cause delays. However, consistent punctuality is vital because it ensures our team meetings start on time and everyone is present to contribute. When you’re late, it disrupts the workflow and places additional pressure on your colleagues.”
Alex: “I understand. I didn’t realize it was causing such an impact. I’ll try to leave my house earlier next time.”
Manager: “I appreciate that. Moving forward, I need you to make a conscious effort to arrive on time every day. Can you commit to doing that starting tomorrow?”
Alex: “Yes. I’ll adjust my schedule to make sure I’m here on time.”
Manager: “Great. If you encounter any issues that might prevent you from being on time, please let me know so we can find a solution together. I’ll check in again next week to see how things are going. Thank you, Alex.”
Alex: “Thanks for understanding, and I appreciate this chance to improve.”
HR tip
A verbal reprimand does not need to be confrontational or presumptuous. There are often underlying circumstances when an employee’s work performance is suffering. The goal is to make the employee aware of the issues and work with them towards a resolution.
How can HR document a verbal reprimand?
Documenting a verbal reprimand is essential for HR professionals to ensure there is a record of the interaction and that the process is transparent and consistent. Here’s how to do it effectively:
- Record the details: Document the date, time, and location of the verbal reprimand and identify the individuals involved, including the person giving the reprimand, the recipient, and any witnesses who might be present.
- Describe the issue: When documenting a verbal reprimand, it’s important to clearly describe the behavior or performance issue that led to it. Here’s how you can effectively do so:
- Be specific: Provide detailed information about the behavior or performance problem. Use solid examples, including dates, times, and specific incidents, to illustrate the issue clearly.
- Focus on observable actions: Describe the behavior objectively, focusing on what was observed rather than making subjective judgments or assumptions.
- Offer guidance or expectations for improvement: Communicate the desired change in behavior or performance expectations. Provide specific recommendations or guidance on how the employee can address the issue and prevent future occurrences.
- Reference to policies: Include references to specific company policies or performance standards that were violated.
- Previous warnings or incidents: Note any previous warnings or related incidents involving the employee. If the employee has received previous warnings, the best practice is to have a witness at subsequent meetings with them.
- Employee acknowledgment: Document the employee’s acknowledgment of the reprimand and understanding of the expectations moving forward.
- Signatures: Obtain signatures from the employee, manager (and witness) acknowledging receipt and understanding of the verbal reprimand.
What to keep in mind
It’s crucial to maintain consistency and fairness when issuing verbal reprimands. Ensure that all employees are treated equitably and that disciplinary actions are based on clear policies and documented evidence. Additionally, provide opportunities for employees to improve their performance or behavior through coaching, training, or supportive resources.